Detection engineering isn’t just about writing rules. It’s about understanding how data behaves, what normal looks like and how attackers blend in with that normality. The Elastic SIEM platform gives analysts great flexibility, but that same freedom can easily lead to noise if it is not grounded in discipline. Building reliable detections require structure – an engineering approach that treats rules and pipelines as living systems instead of static configurations.
This best practices guide for detection engineering in Elastic SIEM looks at the patterns, habits and design choices that separate effective detection programs from reactive ones.
The Mindset Behind Detection Engineering
Many teams still treat detections as a list of signatures to maintain. That model doesn’t scale. Attackers evolve faster than static rule sets and every new detection adds to the operational load. Detection engineering reframes the process as iterative learning i.e. building, testing, tuning and retiring detections continuously.
Elastic SIEM makes this approach feasible because it’s open, transparent and tightly integrated with Elastic’s broader observability stack. Rules and threat intelligence live in the same searchable environment. Analysts can pivot from alerts to raw telemetry without even leaving the interface. The result is faster hypothesis testing and shorter feedback loops.
But tools do not replace discipline. The real strength of Elastic SIEM appears when teams follow clear design principles that keep detections measurable and meaningful.
Core Principles for Detection Engineering
A detection built in Elastic SIEM should do three things: reduce noise, improve context and improve analyst decision-making. Everything else – dashboards, alerts, metrics – exists to support those goals.
1. Focus on Data Quality Before Detection Quantity
Elastic SIEM’s flexibility means it can ingest almost anything. But bad data only produces bad results faster. Spend time validating field mappings, normalising sources and enriching telemetry. Use Elastic Common Schema (ECS) as your baseline to standardise events across systems.
2. Define Detection Goals in Hypotheses, Not Rules
Instead of starting with “What rule do we need?”, begin with “What behaviour are we trying to confirm or disprove?” This small shift prevents rule sprawl. Elastic SIEM’s query-driven nature supports this approach perfectly – each rule becomes an expression of an investigative hypothesis instead of a static condition.
3. Iterate and Measure
Every rule has a lifecycle. It should be built, tested, measured and either improved or retired. Elastic SIEM’s built-in rule execution metrics—like hit counts, false positive rates and alert suppression stats—make this process measurable. Treat every rule as an experiment.
4. Correlate Instead of Over-Alerting
Avoid the temptation to alert on every indicator. Correlate signals across data sources. For example, combine process creation logs and authentication data. Elastic SIEM’s correlation rules let you connect these signals in real time, reducing noise while improving fidelity.
5. Build for Transparency and Reuse
Document your logic. Store rule definitions in Git. Share them internally or through Elastic’s open detection repositories. Transparency strengthens consistency and helps junior analysts learn from proven models.
The Detection Engineering Framework
To make these principles actionable, it helps to follow a structured framework.
The Five Stages of Detection Engineering in Elastic SIEM
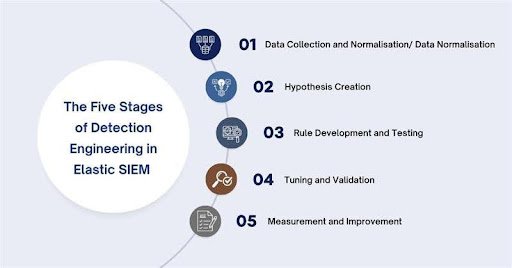
1.Data Collection and Normalisation/ Data Normalisation
Begin with identifying reliable data sources. Use Beats or Elastic Agent to collect logs, then align them with ECS. The cleaner the data, the less time analysts spend fixing broken queries.
2.Hypothesis Creation
Formulate what you want to detect. For instance, “detect lateral movement using SMB” or “identify abnormal service creation events.” Each hypothesis should tie back to a tactic in frameworks like MITRE ATT&CK.
3.Rule Development and Testing
Write detection logic using KQL or EQL within Elastic SIEM. Test it against both benign and malicious datasets to ensure precision. Tag each rule with metadata—owner, version, use case, and severity.
4.Tuning and Validation
Deploy the rule in a staging environment. Analyse alert frequency and false positives. Elastic SIEM’s rule tuning options—filters, exceptions, and threshold conditions—make refinement simple.
5.Measurement and Improvement
Review detection performance regularly. Archive underperforming rules, merge redundant ones, and expand coverage where patterns emerge. Treat this as continuous engineering, not a one-off setup.
Leveraging Elastic SIEM’s Strengths
Elastic SIEM offers several features that directly support mature detection engineering practices.
- Detection Rules as Code: Rules can be exported, version-controlled, and shared, making collaboration between teams simple.
- Machine Learning Jobs: Elastic’s ML models identify anomalies in user or network behaviour without fixed thresholds. This complements rule-based detection rather than replacing it.
- Event Correlation and Timeline Analysis: Investigators can visualise how multiple alerts relate, building richer narratives from what would otherwise be fragmented data.
- Integration with Threat Intel Feeds: Elastic allows automated enrichment from open or commercial feeds, helping analysts contextualise detections faster.
Used together, these features create a strong environment where engineering meets analysis and every detection is backed by data and every alert serves a purpose.
Avoiding Common Detection Pitfalls
Detection engineering in Elastic SIEM can fail quietly if certain traps go unnoticed.
- Over-reliance on Vendor Rules: The built-in detection library is strong, but it’s not tailored to every environment. Use it as reference material, not gospel.
- Ignoring Data Latency: Real-time detection depends on timely ingestion. If log forwarding lags, alerts will always trail behind incidents. Monitor pipeline performance continuously.
- Unstructured Alert Review: Without ownership and review cycles, alerts accumulate and lose meaning. Assign each rule an owner and define how often it should be validated.
- Neglecting Contextual Enrichment: Plain logs tell limited stories. Add hostnames, usernames, and geo data to detections to make decisions faster.
Elastic SIEM gives the tools to fix these issues, but success depends on process maturity.
Aligning Detections with MITRE ATT&CK
Mapping detections to MITRE ATT&CK isn’t a compliance exercise. It’s a clarity exercise. It helps teams see where they have strong coverage and where gaps exist.
Elastic SIEM’s detection rules often include built-in ATT&CK mappings, but custom ones should follow the same pattern. Tagging each rule with a tactic and technique improves reporting and facilitates red-blue team collaboration.
Regularly review your detection map. When new techniques appear in ATT&CK updates, assess whether your current detections address them. The process keeps detection engineering grounded in real adversary behaviours rather than arbitrary events.
The Role of Automation in Detection Engineering
Automation supports detection engineering; it doesn’t replace it. Elastic SIEM’s integrations with Elastic Security Orchestration (SOAR) or other response tools allow routine triage tasks to run automatically. Still, every automated action should trace back to a verified detection rule.
The balance lies in keeping humans focused on investigation, not administration. When detections are reliable and context-rich, automation becomes safe. When they’re noisy, it amplifies chaos. The difference comes from disciplined engineering upstream.
Conclusion
Detection engineering in Elastic SIEM is less about writing clever queries and more about designing resilient systems that evolve with your threat landscape. A disciplined approach—rooted in clean data and measurable outcomes—turns the SIEM from a reactive alert engine into a proactive intelligence platform.
CyberNX can help organisations build and maintain this maturity. They help you design and implement Elastic SIEM according to best practices on Elastic Cloud, on-premises, or public cloud to meet your business requirements.
Effective detection engineering doesn’t happen by chance. It’s built, tested, tuned and lived. With the right foundation, Elastic SIEM becomes not just a tool, but an engine for insight.